How-to : Windows Event Collector: DNS Event Log Forwarding
Tomasz Jagiello strikes back as guest writer 🙂 This time on Windows Event Collector configuration for DNS Event Log forwarding. Very good how-to with detailed configuration.
Design where via Group Policy a Domain Controller group will be configured to forward DNS Server events to a single collector.
To test and demonstrate Event Log Forwarding I built simple Lab environment:
- 2x Domain Controllers (DC1, DC2)
- 1x Event Collector (SRV1).
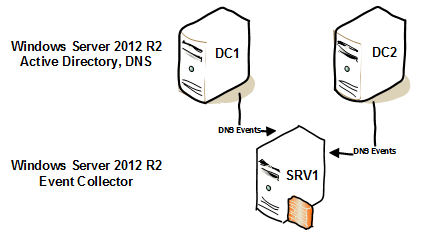
Create the Event Forwarding Subscription on the Event Collector (SRV1)
In the Windows Event Forwarding architecture, the subscription definition is held and maintained on the Collector in order to reduce the number of touch-points in case a subscription needs to be created or modified.
Creating the subscription can be accomplished through the Event Viewer user interface.
- Select the Create Subscription (2) action when the Subscriptions (1) branch is highlighted
- Say Yes (3) to start Windows Event Collector Service
- Type Subscription Name (4), set Subscription type to Source computer initiated (5), click on Select Computer Groups
- Click Add Domain Computers (6) and select Domain Controllers group, accept changes clicking OK
- Click on Select Events… button, change to XML tab, tick Edit query manually (7) and type:
<QueryList>
<Query Id="0" Path="DNS Server">
<Select Path="DNS Server">*[System[(Level=1 or Level=2 or Level=3 or Level=4 or Level=0 or Level=5)]]</Select>
</Query>
</QueryList>
- Click OK
- Click on Advanced… button and select Minimize Latency (8) to forward events as quickly as possible, OK and OK to complete
Change the Forwarded Events Maximum log size on the Event Collector (SRV1)
- Right click on the Forwarded Events log and choose Properties
- Change the Maximum log size accordingly to your needs
Configure Group Policy to enable Windows Remote Management on the Source Computers (clients) (DCs)
Create a new Group Policy to be linked to your client machines (Event sources); in our case this will be Domain Controllers OU.
This Group Policy is going to do three things:
- Make sure that the Windows Remote Management (WS-Management) service is running
Computer Configuration \ Policies \ Windows Settings \ Security Settings \ System Services \ Windows Remote Management (WS-Management) Service
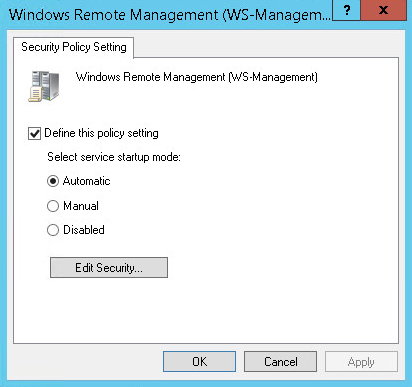
Set to Automatic
- Enable WinRM on the client as well as configure a Listener that will accept packets from ANY source.
Computer Configuration \ Policies \ Administrative Templates \ Windows Components \ Windows Remote Management (WinRM) \ WinRM Service \ Allow remote server management through WinRM
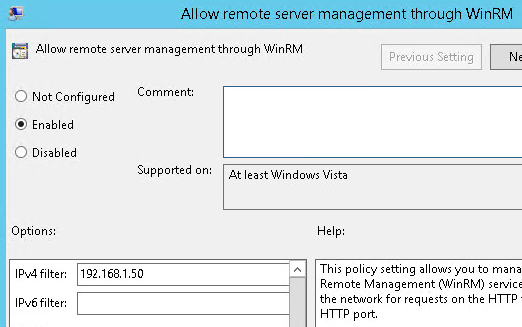
Set to Enabled
IPv4 filter: <for security purposes configure only specific IP Addresses or ranges>
IPv6 filter: blank
- Tell the clients where to connect to for their Windows Event Forwarding configuration
Computer Configuration \ Policies \ Administrative Templates \ Windows Components \ Event Forwarding \ Configure target Subscription Manager
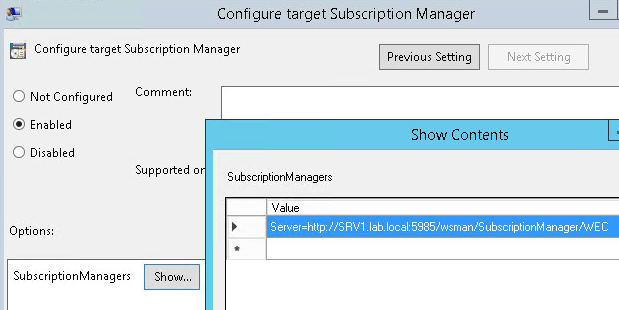
Set to Enabled
SubscriptionManagers: Server=http://<FQDN of your upstream Windows Event Collector Server>:5985/wsman/SubscriptionManager/WEC
Configure the Event Log Readers Group on the Source Computers (clients) (DCs)
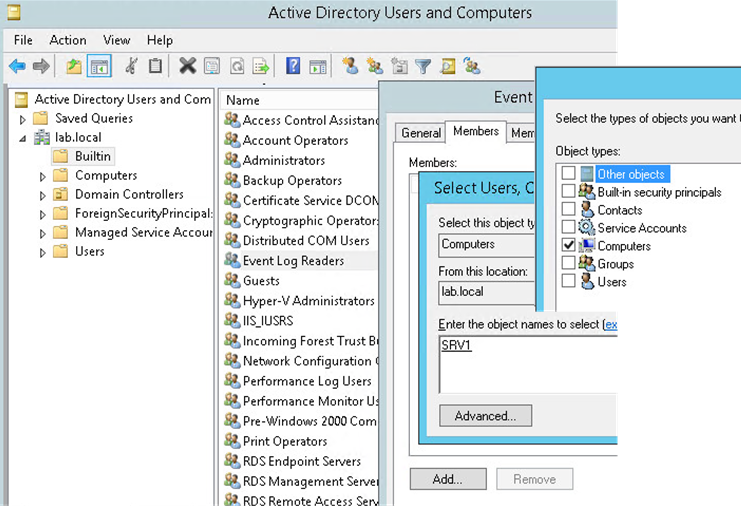
Since our source computers are Domain controllers open ADUC, expand domain and search Builtin for Event Log Readers group.
Go to Properties and Members and add your Event Collector Server (SRV1)
Reference documents
https://www.loggly.com/ultimate-guide/centralizing-windows-logs/
https://www.petri.com/configure-event-log-forwarding-windows-server-2012-r2
http://www.vkernel.ro/blog/how-to-configure-windows-event-log-forwarding
http://www.vkernel.ro/blog/remote-group-policy-update-in-windows-server-2012
https://www.petri.com/configure-event-log-forwarding-windows-server-2012-r2
