Current expectations from all type of systems and services is to be available without any disruption. One of mission critical systems is gateway/firewall. Of course you can use multiple products available on the market. One of them is openSUSE, which is perfect to act as gateway/firewall between Internet and production systems. So, how to provide redundancy for openSUSE and same time be able to keep it up-to-date without any disruption for production systems?
openSUSE 13.2 with keepalived provides all technology required to make your firewall high-available.
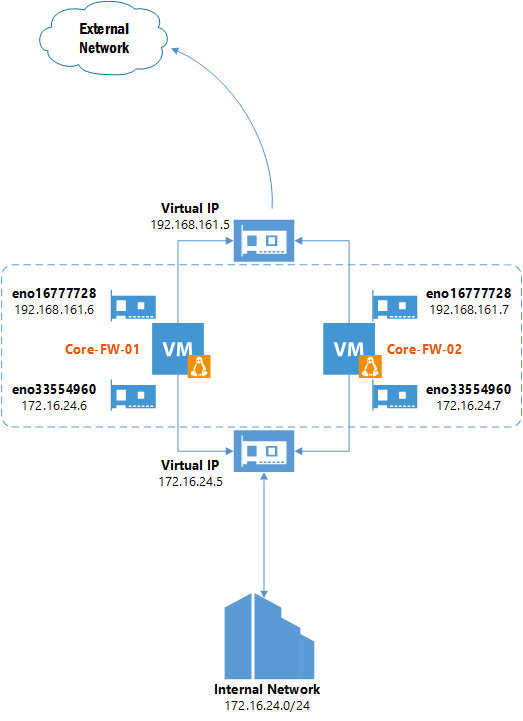
Here is diagram of Lab created to configure and test openSUSE with keepalived:
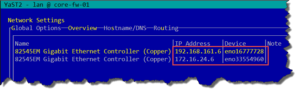
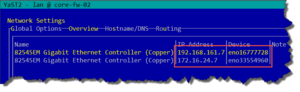
Network configuration on Core-FW-01
Network interfaces configuration
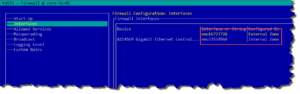
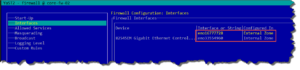
Interface Zone assignment in Firewall settings
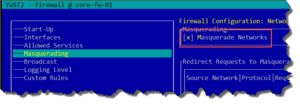
Masquerading enabled to allow NAT
Network configuration on Core-FW-02
Network interfaces configuration
Interface Zone assignment in Firewall settings
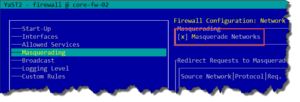
Masquerading enabled to allow NAT
Once network parameters and settings are correct we can move on to keepalived configuration.
Configuration of keepalived on Core-FW-01
/etc/keepalived/keepalived.conf
vrrp_sync_group {
group {
fw-cluster-eno16777728
fw-cluster-eno33554960
}
}
vrrp_instance fw-cluster-eno16777728 {
state MASTER
interface eno16777728
virtual_router_id 20
priority 100
virtual_ipaddress {
192.168.161.5/24 brd 192.168.161.255 dev eno16777728
}
}
vrrp_instance fw-cluster-eno33554960 {
state MASTER
interface eno33554960
virtual_router_id 30
priority 100
virtual_ipaddress {
172.16.24.5/24 brd 172.16.24.255 dev eno33554960
}
}
Configuration of keepalived on Core-FW-02
/etc/keepalived/keepalived.conf
vrrp_sync_group {
group {
fw-cluster-eno16777728
fw-cluster-eno33554960
}
}
vrrp_instance fw-cluster-eno16777728 {
state BACKUP
interface eno16777728
virtual_router_id 20
priority 100
virtual_ipaddress {
192.168.161.5/24 brd 192.168.161.255 dev eno16777728
}
}
vrrp_instance fw-cluster-eno33554960 {
state BACKUP
interface eno33554960
virtual_router_id 30
priority 100
virtual_ipaddress {
172.16.24.5/24 brd 172.16.24.255 dev eno33554960
}
}
Summary
Now you can enjoy your firewall HA.