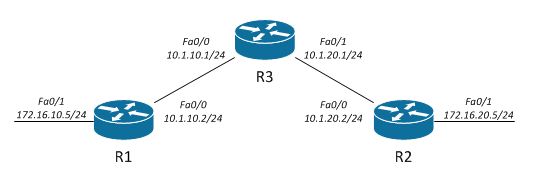
This is simple Lab environment I built when was working on IPsec VPN tunnel between our internal network environment and 3rd party vendor systems. As we had some issues with establishing IPsec communication, to make sure that everything is fine on my side I start replicating live environment in Lab. To build test environment quick I use GNS3 as platform to run Dynamips hypervisor for IOS. That speeds up whole process of preparation and testing.

GNS3 Lab files for that article are available here.
Software used to build LAB
- GNS3 0.8.1 VirtualBox Edition as platform to run Dynamips hypervisor to run Cisco IOS
- IOS image c3600-a3jk9s-mz.124-25c.bin
Routers and their roles
R1 – Router located in Site A
- fa0/0 – interface connected to public network – in LAB 10.1.10.0/24 network is simulating public network. In real scenarion fa0/0 is connected to Internet and has public IP address
- fa0/1 – interface connected to private network
R2 – Router located in Site B
- fa0/0 – interface connected to public network – in LAB 10.1.20.0/24 network is simulating public network. In real scenarion fa0/0 is connected to Internet and has public IP address
- fa0/1 – interface connected to private network
R3 – Router which is acting as Internet 🙂
- fa0/0 – interface connected to 10.1.10.0/24 network, which is “public” network for Site A
- fa0/1 – interface connected to 10.1.20.0/24 network, which is “public” network for Site B
Folder structure for GNS3 project
- F:\GNS3\Images – folder which contains IOS images for GNS3 and Dynamips hypervisor
- F:\GNS3\LAB Files\IPsec L2L – folder for GNS3 project file – topology.net
- F:\GNS3\LAB Files\IPsec L2L\configs – folder for router configuration files – r1.cfg, r2.cfg, r3.cfg
NOTE: Presented folder structure is only example and might be different in your case. It depends on GNS3 configuration. I just show example how I arranged files. Make sure that you will change paths in topology.net file in case example will be placed in different folder structure.
topology.net
autostart = False [127.0.0.1:7200] workingdir = F:\GNS3\Temp udp = 10000 [[3660]] image = F:\GNS3\Images\c3660-a3jk9s-mz.124-25c.bin idlepc = 0x6057e6c4 ghostios = True chassis = 3660 [[ROUTER R1]] model = 3660 console = 2000 cnfg = configs\R1.cfg f0/0 = R3 f0/0 x = -227.0 y = -119.0 [[ROUTER R2]] model = 3660 console = 2003 cnfg = configs\R2.cfg f0/0 = R3 f0/1 x = 134.0 y = -118.0 [[ROUTER R3]] model = 3660 console = 2004 cnfg = configs\R3.cfg f0/0 = R1 f0/0 f0/1 = R2 f0/0 x = -42.0 y = -172.0 [GNS3-DATA] configs = configs [[NOTE 1]] text = f0/1 x = 71.240543865 y = 33.7328941404 interface = R3 f0/1 [[NOTE 2]] text = f0/0 x = -5.45310453764 y = 33.0162948135 interface = R3 f0/0 [[NOTE 3]] text = f0/0 x = -5.24054386499 y = 10.2671058596 interface = R2 f0/0 [[NOTE 4]] text = f0/0 x = 71.4531045376 y = 10.9837051865 interface = R1 f0/0
R1.cfg
! version 12.4 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname R1 ! boot-start-marker boot-end-marker ! no aaa new-model memory-size iomem 5 ! ip cef ! crypto isakmp policy 10 encr 3des authentication pre-share group 2 crypto isakmp key lab123 address 10.1.20.2 ! crypto ipsec transform-set TRANSFORM_SET_1 esp-3des esp-md5-hmac ! crypto map CRYPTO_MAP_1 5 ipsec-isakmp set peer 10.1.20.2 set transform-set TRANSFORM_SET_1 match address L2L_R2 ! interface FastEthernet0/0 ip address 10.1.10.2 255.255.255.0 duplex auto speed auto crypto map CRYPTO_MAP_1 ! interface FastEthernet0/1 ip address 172.16.10.5 255.255.255.0 duplex auto speed auto ! ip http server no ip http secure-server ip forward-protocol nd ip route 0.0.0.0 0.0.0.0 10.1.10.1 ! ip access-list extended L2L_R2 permit ip 172.16.10.0 0.0.0.255 172.16.20.0 0.0.0.255 ! control-plane ! line con 0 line aux 0 line vty 0 4 login ! end
R2.cfg
! version 12.4 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname R2 ! boot-start-marker boot-end-marker ! no aaa new-model memory-size iomem 5 ! ip cef ! crypto isakmp policy 10 encr 3des authentication pre-share group 2 crypto isakmp key lab123 address 10.1.10.2 ! crypto ipsec transform-set TRANSFORM_SET_1 esp-3des esp-md5-hmac ! crypto map CRYPTO_MAP_1 5 ipsec-isakmp set peer 10.1.10.2 set transform-set TRANSFORM_SET_1 match address L2L_R2 ! interface FastEthernet0/0 ip address 10.1.20.2 255.255.255.0 duplex auto speed auto crypto map CRYPTO_MAP_1 ! interface FastEthernet0/1 ip address 172.16.20.5 255.255.255.0 duplex auto speed auto ! ip http server no ip http secure-server ip forward-protocol nd ip route 0.0.0.0 0.0.0.0 10.1.20.1 ! ip access-list extended L2L_R2 permit ip 172.16.20.0 0.0.0.255 172.16.10.0 0.0.0.255 ! control-plane ! line con 0 line aux 0 line vty 0 4 login ! end
R3.cfg
! version 12.4 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname R3 ! boot-start-marker boot-end-marker ! no aaa new-model memory-size iomem 5 ! ip cef ! interface FastEthernet0/0 ip address 10.1.10.1 255.255.255.0 duplex auto speed auto ! interface FastEthernet0/1 ip address 10.1.20.1 255.255.255.0 duplex auto speed auto ! ip http server no ip http secure-server ip forward-protocol nd ! control-plane ! line con 0 line aux 0 line vty 0 4 login ! end
When Lab is up and running
Ping from Site A to Site B
R1#ping 172.16.20.5 source fa0/1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.20.5, timeout is 2 seconds: Packet sent with a source address of 172.16.10.5 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 40/44/60 ms R1#
R1 – sh crypto isakmp sa
R1#sh crypto isakmp sa dst src state conn-id slot status 10.1.10.2 10.1.20.2 QM_IDLE 1 0 ACTIVE R1#
R1 – sh crypto ipsec sa
R1#sh crypto ipsec sa
interface: FastEthernet0/0
Crypto map tag: CRYPTO_MAP_1, local addr 10.1.10.2
protected vrf: (none)
local ident (addr/mask/prot/port): (172.16.10.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (172.16.20.0/255.255.255.0/0/0)
current_peer 10.1.20.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 19, #pkts encrypt: 19, #pkts digest: 19
#pkts decaps: 19, #pkts decrypt: 19, #pkts verify: 19
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 10.1.10.2, remote crypto endpt.: 10.1.20.2
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0x93DB68FA(2480630010)
inbound esp sas:
spi: 0x47E2A9C0(1206036928)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: SW:1, crypto map: CRYPTO_MAP_1
sa timing: remaining key lifetime (k/sec): (4396282/322)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x93DB68FA(2480630010)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: SW:2, crypto map: CRYPTO_MAP_1
sa timing: remaining key lifetime (k/sec): (4396282/267)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
R1#
Ping from Site B to Site A
R2#ping 172.16.10.5 source fa0/1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.10.5, timeout is 2 seconds: Packet sent with a source address of 172.16.20.5 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 36/40/48 ms R2#
R2 – sh crypto isakmp sa
R2#sh crypto isakmp sa dst src state conn-id slot status 10.1.10.2 10.1.20.2 QM_IDLE 1 0 ACTIVE R2#
R2 – sh crypto ipsec sa
R2#sh crypto ipsec sa
interface: FastEthernet0/0
Crypto map tag: CRYPTO_MAP_1, local addr 10.1.20.2
protected vrf: (none)
local ident (addr/mask/prot/port): (172.16.20.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (172.16.10.0/255.255.255.0/0/0)
current_peer 10.1.10.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 19, #pkts encrypt: 19, #pkts digest: 19
#pkts decaps: 19, #pkts decrypt: 19, #pkts verify: 19
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 10.1.20.2, remote crypto endpt.: 10.1.10.2
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0xAAA62BF(178938559)
inbound esp sas:
spi: 0x583DB35F(1480438623)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2003, flow_id: SW:3, crypto map: CRYPTO_MAP_1
sa timing: remaining key lifetime (k/sec): (4595568/3187)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xAAA62BF(178938559)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2004, flow_id: SW:4, crypto map: CRYPTO_MAP_1
sa timing: remaining key lifetime (k/sec): (4595568/3175)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
R2#