Whole idea for that article came from real environment. At home I have DrayTek Vigor 2850n as my broadband router (and in fact it is really nice piece of equipment). Same time I’m using some Cisco equipment located in remote Lab for testing purposes. Remote Lab is connected to Intrenet and before to get access to devices and systems located there I was using EzVPN. However, as Lab has Cisco ISR as main router I thought, why not to establish L2L IPsec between my home network and remote Lab. Now, question how to do that. I have DrayTek on one end and Cisco ISR on the other. After few attempts, mis-configurations and troubleshooting it did work quite well in fact. So, here it is.
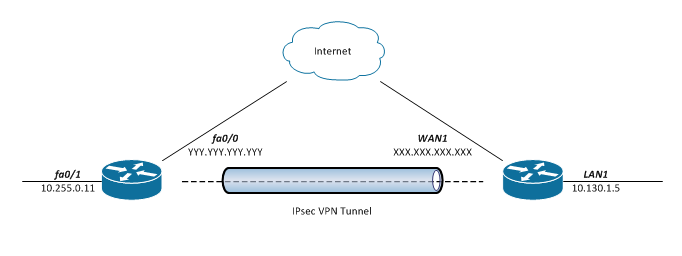
Here is what needs to be achieved:
Equipment available:
- Cisco ISR 2811 – on the left side of the diagram – internal network 10.255.0.0/24
- DrayTek Vigor 2850n – on the right side of the diagram – internal network 10.130.1.0/24
Goal:
- Establish IPsec VPN Tunnel between Cisco and DrayTek to make communication available between 10.255.0.0/24 and 10.130.1.0/24.
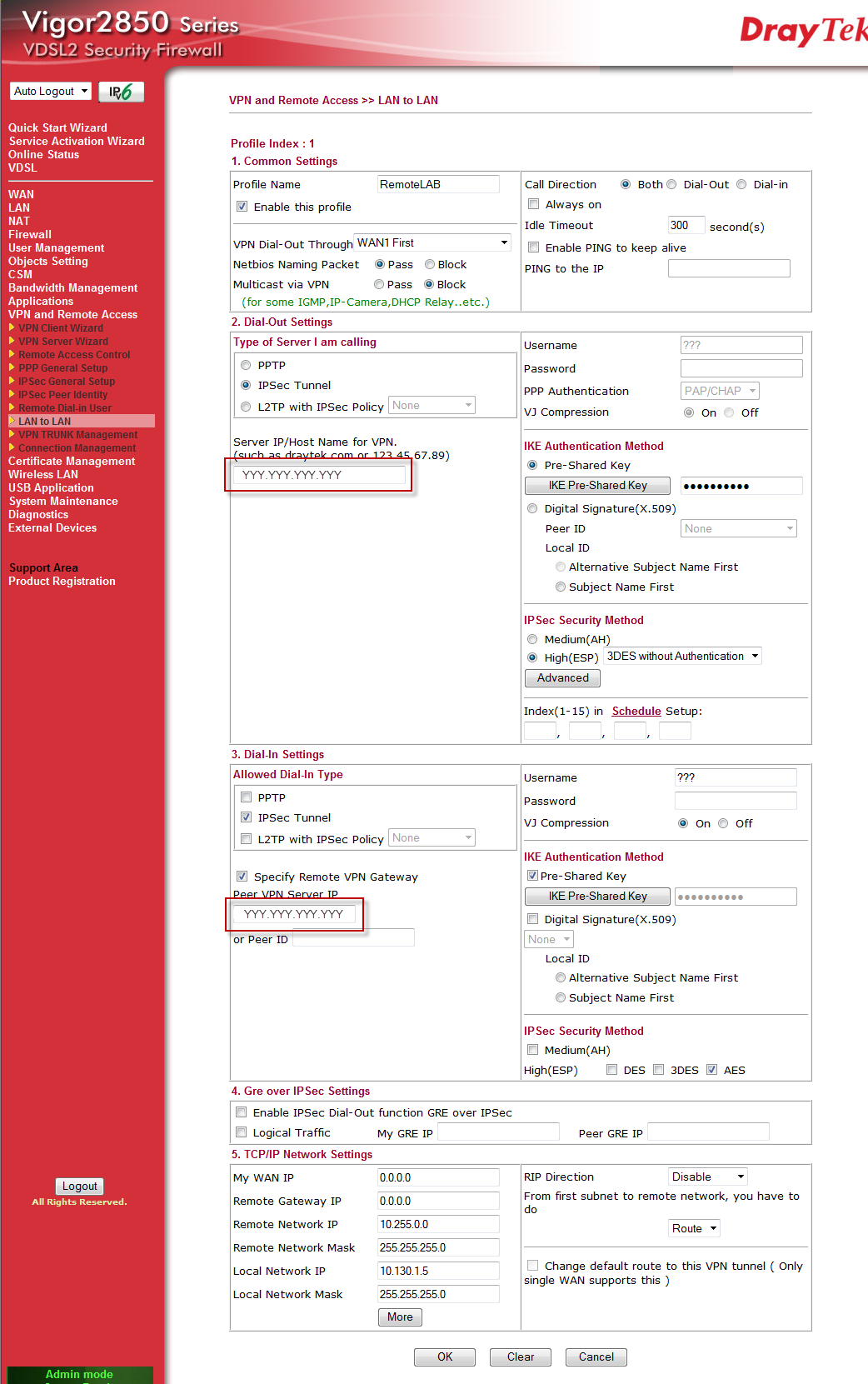
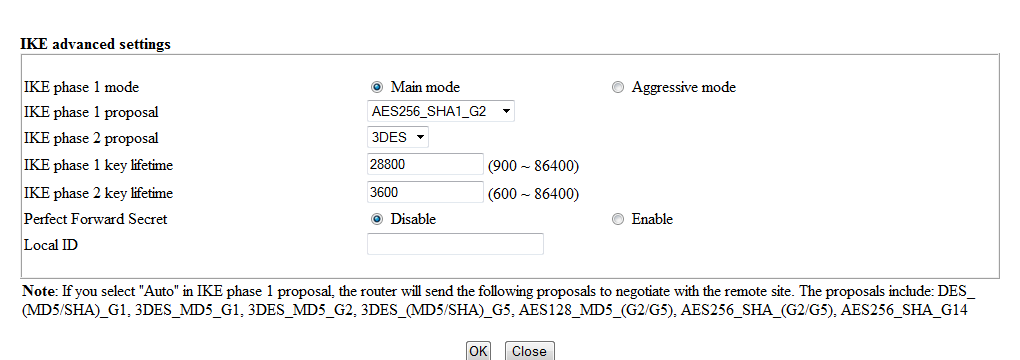
Configuration on Draytek Vigor 2850n
Configuration on lab-r01 – Cisco ISR 2811
service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname lab-r01 ! logging buffered 51200 debugging enable secret enable123 ! no aaa new-model ! resource policy ! ip cef ! ip domain name domain.lab ! voice-card 0 no dspfarm ! username labadmin password abc123 ! crypto isakmp policy 10 encr aes 256 hash sha authentication pre-share group 2 crypto isakmp key abc123key address XXX.XXX.XXX.XXX no-xauth ! crypto ipsec transform-set dtek-set esp-3des crypto ipsec df-bit clear ! crypto map LAB_TO_DTEK 20 ipsec-isakmp set peer XXX.XXX.XXX.XXX set transform-set dtek-set match address LabDT ! interface FastEthernet0/0 description ### Uplink to ISP ### ip address YYY.YYY.YYY.YYY 255.255.255.240 ip nat outside ip virtual-reassembly duplex auto speed auto crypto map LAB_TO_DTEK ! interface FastEthernet0/1 description ### LabNET ### ip address 10.255.0.11 255.255.255.0 ip nat inside ip virtual-reassembly duplex auto speed auto ! ip route 0.0.0.0 0.0.0.0 ZZZ.ZZZ.ZZZ.ZZZ ! no ip http server no ip http secure-server ip nat inside source route-map NoNat interface FastEthernet0/0 overload ! ip access-list extended LabDT permit ip 10.255.0.0 0.0.0.255 10.130.1.0 0.0.0.255 ip access-list extended NoNat deny ip 10.255.0.0 0.0.0.255 10.130.1.0 0.0.0.255 permit ip 10.255.0.0 0.0.0.255 any ! route-map NoNat permit 10 match ip address NoNat ! control-plane ! line con 0 login local line aux 0 line vty 0 4 login local transport input telnet line vty 5 15 login local transport input telnet ! scheduler allocate 20000 1000 ! end lab-r01#
Summary
Once configuration is done on both sides internal network can communicate without any problems 🙂